Phishing and other dangerous emails
I have replied to a phishing mail and given out my account details/"been hacked" - what should I do?
Read more further down the page.
ATTENTION! When the university's IT or security staff suspect that account information has been stolen, the account in question will be blocked immediately to reduce the risks. IT-support can then instruct you on how to change the password to be able to use the account again.
Below we advise you on how you can proceed to reduce the risk of being affected.
Read the email carefully
Do you get a bad feeling when you read an email you received? Phishers are often looking for passwords, credit card numbers or other sensitive information.
Ask for confirmation
You can always contact the sender by calling or sending a new email (don't reply to the one you just received) to confirm that the request is correct and not a scam attempt.
The image below shows what such a phishing email might look like. Here, the fraudster does not ask for your details directly in the email. Instead, they try to lure you onto a web page, in this case a fake version of LinkedIn, where you are then asked to log in with your details. If you complete the login, the unknown phisher has managed to access your login details.
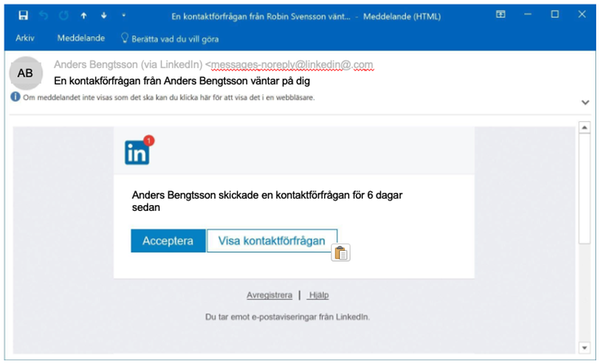
Detta är ett exempel på ett phishing-mejl. De kan se ut på många andra sätt.
Review the sender
It is easy for those who send malicious e-mail to change the sender name. Therefore, you should never trust that it corresponds to reality. Instead, you need to research the sender address. You may need to click on the sender's name to see the actual address.
Is the domain name reasonable?
The email address can be split into two parts, as shown in the image below. We are interested in what comes after the @ sign because we are going to review the domain name to see the real sender. Let's say you receive an email from Anders.Bengtsson@company.com. The domain name for the sender is then company.com
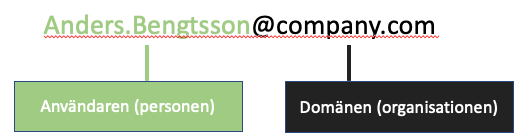
This is an example of a phishing email. They can look in many other ways.
But if get an email from Anders.Bengtsson@company.com.login-fulsite.nu ? Now it shouldn't feel as safe.
To understand the structure of the email address, we break the domain name down into parts. The different parts become clear in the image below.
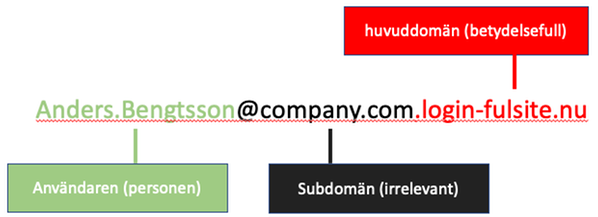
Phishers often create their own subdomains. At first glance, it may look like you received the email from company.com. But the subdomains are irrelevant. Inspect the main domain and the top-level domain, in this case login-fulsite.nu. When you separate this part from the rest of the email address, it becomes clear that you are dealing with a likely phisher. Also keep in mind that fraudsters can register domain names that are similar to the legitimate organization's. An example is company.net or companie.com instead of company.com.
Reveal shady links
Does the email contain a link that looks suspicious? You should never click on links that you did not request or that look unreasonable. If the sender asks you to provide a username and password via a link in an email, it is almost always a fraud. Contact the alleged sender and ask.
The link may be camouflaged
A link consists of two parts – a link text, which is what appears in the email, and the link itself, which is where you actually go if you click on the link. You can easily review the link without risking entering the web page. On the computer you hover the mouse pointer over/on the link and on the mobile you hold your finger on the link without letting go. The real link will then be displayed. Does the link go to the expected webpage/location? If not, don't click on the link text/link.
I have replied to a phishing mail and given out my account details/"been hacked" - what should I do?
- immediately change your passwords A and B, and
- directly contact the security department security@uu.se and
- call IT Support on 018-471 4400
If your account has been blocked/suspended, go to the nearest reception to collect a new activation code to renew your passwords.
You will need to prove your identity to receive the activation code.
More information on how to change your password.
Learn more about phishing
